Virtual CISO
Maximize Your Cybersecurity at a Fraction of the Cost
Finding the right security team with the expertise and leadership to build a winning information security strategy can be a real headache.
of organizations are not confident their teams would be able to handle a data breach.
WHY NODECYPHER VCISO?
That’s where NodeCypher’s Virtual Chief Information Security Officer (Virtual CISO) comes in. We take the hassle out of hiring by giving you on-demand access to seasoned security professionals, whenever you need them. Think of them as an extension of your team, assessing cyber-risks, formulating the essential policies, procedures, building controls to enhance your security posture and to meet compliance standards.
WHY
HIRE A vCISO?
Cost-Effective
Access top-tier security expertise without the high overhead of a full-time hire.
Expert Guidance
Benefit from our team's extensive experience in building, managing, and improving cybersecurity programs tailored to your organizational needs.
Proactive Protection
Identify and address potential threats before they become critical issues and proactively protect your assets.
Regulatory Compliance
Ensure your business adheres to industry standards and regulations.
Proven Result
Expect consistent, high-quality service and deliverables that bolster your cybersecurity efforts and facilitate ongoing improvement.
Customer Centric Approach
Technical expertise with a customer-centric approach, making cybersecurity accessible and effective for businesses of all sizes.
WHO
NEEDS A VCISO?
Overwhelmed security teams
Enterprises may have internal security teams but need additional support.
Focus on core business
Startups often prioritize product development and sales over security.
Seasonal needs
Organizations with seasonal needs or project-based work may need intermittent security support.
Preparing for an audit
Organizations needing expect guidance for vital audits like SOC2, ISO27001 or industry-specific ones
Stuck on compliance?
Organizations needing help in achieving compliance with HIPAA, NIST-CSF, GDPR etc.
HOW
IT WORKS?
WEEK 1-4
Foundation and Assessment
Initial Consultation
We delve into your business, understanding your goals, security posture, and specific concerns.
Vulnerability Assessment
Our experts conduct a thorough scan to identify potential weaknesses in your systems and networks.
Employee Cybersecurity Training
We empower your team with the knowledge to recognize and prevent cyber threats.
Phishing Simulation
We test your employees' awareness through simulated phishing attacks to identify training needs.
WEEK 5-12
Deep Dive and Action Plan
Comprehensive Security Assessment
We perform a rigorous 60-point assessment to benchmark your security against industry best practices.
Platform-Specific Security Review
For Microsoft or Google users, we conduct a tailored security evaluation.
Customized Security Roadmap
Based on our findings, we develop a prioritized action plan to address identified vulnerabilities and improve your security posture.
Ongoing Communication
Regular check-ins ensure alignment with your business objectives and address emerging threats.
Real-Time Visibility and Control
Our vCISO program provides unparalleled insight and control over your organization’s cybersecurity posture through our advanced assessment and compliance portal.
Key features include:
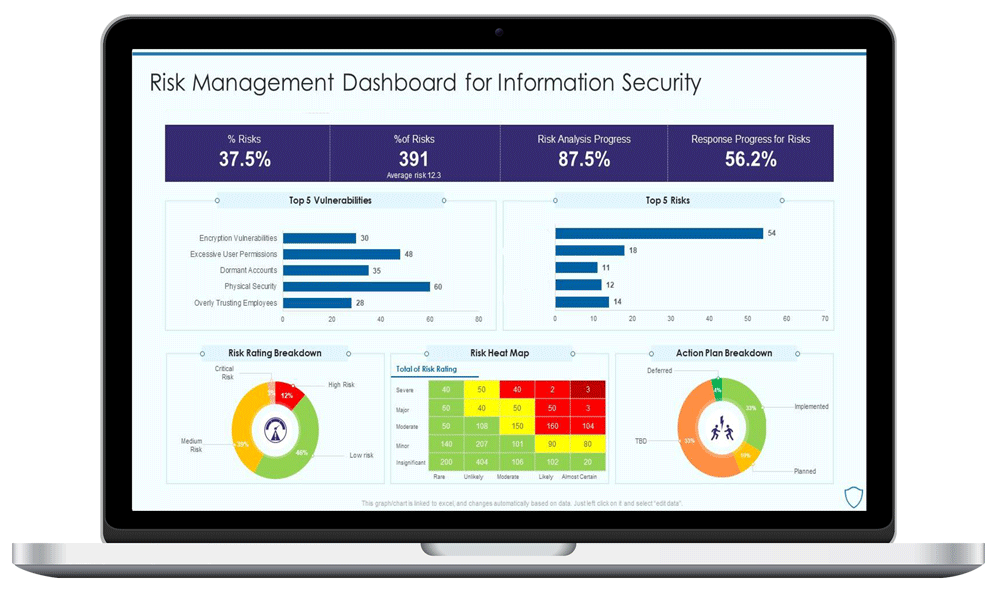
-
Clear Accountability:
Assigned controls for precise responsibility. -
Executive-Level Overview:
Intuitive dashboards for real-time performance metrics. -
Centralized Documentation:
Secure repository for essential security documents and evidence. -
Efficient Workflow:
Automated reminders to streamline tasks and deadlines. -
Third-Party Risk Management:
Comprehensive vendor due diligence assessments and reporting. -
Continuous Improvement:
Our cloud-based platform, coupled with expert guidance, ensures your security program evolves with your business.
WHAT'S
INCLUDED IN VCISO SERVICES
Risk Assessment and Compliance
Conduct thorough gap assessments and compliance evaluations to identify vulnerabilities and ensure compliance.
Vulnerability Management
Regular vulnerability scans and penetration testing to identify and mitigate threats.
Policy and Procedure Optimization
Align your security policies with industry best practices and regulatory mandates.
Audit Support
Provide comprehensive support for audits and evaluations.
Incident Preparedness
Prepare for the unexpected with tabletop exercises and incident response planning.
Security Team Empowerment
Define roles and responsibilities to enhance your team's effectiveness.
Third-Party Risk Management
Assessment and management of risks associated with vendors and suppliers.
Real-Time Visibility
Leverage advanced GRC dashboards for continuous monitoring and actionable insights into your security program's performance.
Employee Education
Comprehensive security awareness training and simulated phishing attacks to build a human firewall.
FAQs
Answers to Common Questions
A vCISO provides top-tier cybersecurity expertise to organizations of all sizes. By offering instant access to high-level talent, vCISO services help businesses save costs and address cybersecurity challenges effectively.
A vCISO can be beneficial for growing startups and medium-sized businesses, especially those in highly regulated industries. If your board requires cybersecurity guidance or you need to fill gaps in your security program without breaking the bank, a vCISO is a valuable option.
vCISO services are priced based on your organization's size and offer significant cost savings compared to hiring a full-time cybersecurity expert.
Our vCISO team collaborates closely with your IT department to assess your cybersecurity needs, develop strategies, and ensure compliance. We provide ongoing support, including security awareness training and incident response assistance.
Absolutely. vCISOs are experts in managing cyber crises. They can help contain damage, inform stakeholders, and improve security measures to prevent future attacks.
Our vCISO services offer essential support for implementing and maintaining a robust cybersecurity program. Ultimately, decision-making and risk management responsibilities remain with your organization.
Contact us to schedule a consultation. We'll discuss your specific needs and develop a customized solution to meet your cybersecurity goals.

